These emails will seemingly come from legitimate companies as well. Please be mindful when opening anything from anyone.
In a nutshell, the .zip file will contain a .PDF that will execute the trojan on your computer thus starting the nightmare that is Cryptolocker. Cryptolocker will then encrypt the following file extensions on your computer.
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd, *.cdr, ????????.jpg, ????????.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c
As you can see this would be a nightmare of a worm to get.
Now after this propagates through your computer you then get this lovely message


100 bucks.
Thats right, $100 smackeroos. I even seen an instance that said $300.00
THINGS YOU CAN DO TO HELP PREVENT THIS
Bleeping Computers .com has a great article on this and how you can prevent this forest fire of a nightmare. Those folks over there are very very good. Read this excerpt from this post by one of their admins:
How to block this infection from running on other computers on your computer.
You can use Software Restriction Policies to block executables from running when they are located in the %AppData% folder, or any other folder, which this thing launches from. See these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
This can also be setup in group policy
File paths of the infection are:
C:\Users\User\AppData\Roaming\{213D7F33-4942-1C20-3D56=8-1A0B31CDFFF3}.exe (Vista/7/8)
C:\Documents and Settings\User\Application Data\{213D7F33-4942-1C20-3D56=8-1A0B31CDFFF3}.exe
So the path rule you want to setup is:
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables from AppData.
With the bundling of Zbot with Cryptolocker, it is now also recommend that you create a rule to block executables running from a subfolder of %AppData%. This can be done with this path rule:
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables from immediate subfolders of AppData.
You can see an alert and event log showing an executable being blocked:
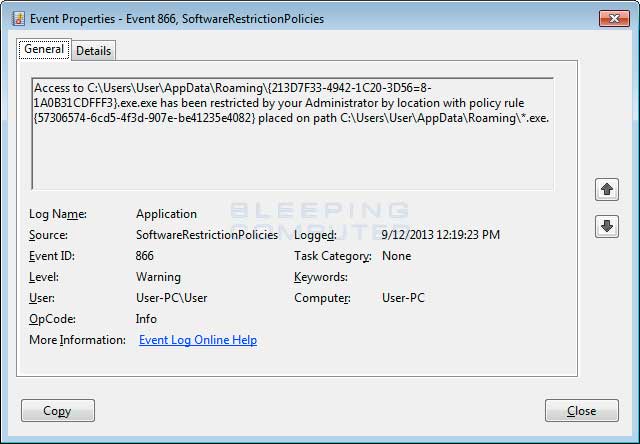
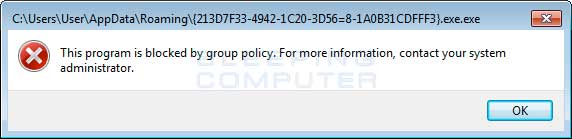
I would like to add that I personally use Acronis as my software backup with an external hard drive.
This is a VERY cheap method to keep your files safe and stored and a very quick recovery if you need to wipe and start over. At any rate, with the prices of Hard Drives so low and software like Acronis so cheap it would benefit everyone to have a nice backup in the event you become infected with terrible stuff like this.

No comments:
Post a Comment